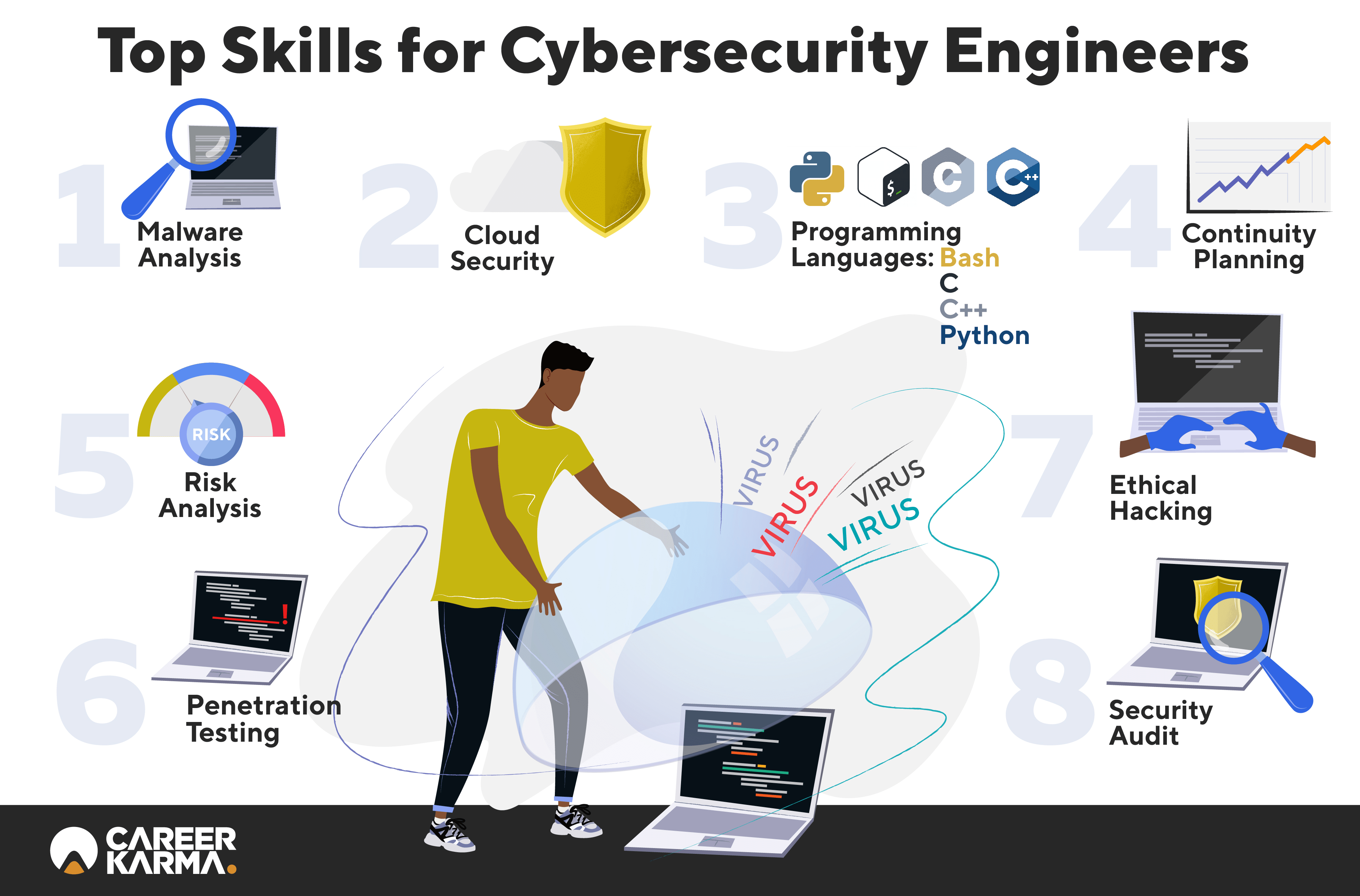
The smart Trick of Third Eye Installation Systems London That Nobody is Discussing
Such usage of CCTV technology has actually fueled privacy issues in several parts of the globe, specifically in those locations in the UK as well as Europe where it has actually ended up being a routine part of cops procedure.
You run a local business on Key Road. There is a lot of foot traffic, specifically at odd hrs of the night. You can't rest and switch on the news at 3 am. The anchor states a "splitting as well as getting in" from looters at your shop. You can not believe your eyes, your heart sinks.
An Unbiased View of Security Systems For Home And Business
In this guide, we will certainly cover all you require to know regarding CCTV. CCTV stands for Closed Circuit Television. Unlike conventional tv, CCTV is a closed-loop system where everything being relayed keeps in-house.
The primary use situation for CCTV is for security purposes. Live footage was the primary attribute for CCTV when it first stood out onto the safety and security scene.
By doing this, we make the most of protecting the premises in real-time in addition to examining archived footage. There are several reasons we will certainly wish to watch out for our environments. Several residences utilize a protection camera to make certain the security of their enjoyed ones. Setting up a video camera outside of your house in multiple ways can dramatically minimize the possibilities of something poor happening.
Third Eye Installation Systems Cctv Installation Can Be Fun For Anyone
The objective right here is to expand video of unwanted trespassers. If you ever before have strangers doing service your house or have a babysitter, a safety and security cam is necessary for protecting your residence when you're not about. Currently that we understand what CCTV is, we can currently ask how does CCTV function? Initially, we require to be conscious of both types of protection video camera systemsanalog and also digital (IP).
The system itself is a bit extra involved and also expensive, yet well worth it in the end - Third Eye Installation Systems intercom intercom systems. It functions likewise as analog, but rather than a DVR, we have an NVR, network video recorder. This simplifies our protection procedure, as the cam replaces the DVR. Currently we can remotely monitor our video live by means of a net link.

Some Known Facts About Alarm Installation London.
Your house and/or company will certainly remain protected. No more will you need to ask what is CCTV as well as exactly how does it work. To learn all points safety and security with video clip monitoringread our blog today!.
This would certainly be specifically beneficial for large facilities or one that holds valuable tools, products or details. As taping video footage, a CCTV system can more information likewise inform you if there is task or movement on a certain cam at a set time. For circumstances, in the dead of evening whilst the service premises in shut as well as staff members have actually gone home (CCTV installation London).
A CCTV system can be utilized for the security of on-site activity, during and also out of working hrs, it can additionally be utilized to assist determine wanted wrongdoers, as well as act as a deterrent to possible trespassers. Need to know the ins as well as outs of just how a CCTV system works? It's not made complex, but it does vary relying on the sort of system you mount and the parts made use of.
Third Eye Installation Systems Intercom Intercom Systems Fundamentals Explained
As pointed out formerly, there are many kinds of CCTV systems with various video cameras that have a variety of usages, such as night vision, thermal imaging and also number plate acknowledgment. The 2 major sorts of system are: Video cameras as well as the rest of the system is tough wired. Wireless No cables are needed as the system functions using a web connection.
Varifocal lens safety video cameras are typically more pricey than fixed lens, yet use the adhering to advantages. With a dealt with lens, your installer would need to physically move and re-install the camera to change the field of vision. With a varifocal lens, the installer important source can adjust the focal size to transform the field of vision.

The Third Eye Installation Systems Burglar Alarms Ideas
We recommend and also make use of varifocal lenses for our setups as we can readjust the lens conveniently and also they are normally much easier to function with. A CCTV video camera iris works in a similar method to a still cam, the much more open the iris is, the brighter the image will certainly be.